19 May 2015 Kerberos authentication and delegation with Tableau and MSSAS
Introduction
Kerberos is a three-way authentication protocol developed by the Massachusetts Institute of Technology (MIT). As of Windows 2000, it has been the default authentication method in Microsoft Windows systems. Tableau Server version 8.3 has supported Kerberos since the release of version 8.3. In this article we will explain how to configure Tableau Server with Kerberos to enable:
– Single Sign-On (SSO) authenticatia on of
– Authentication delegation to Microsoft SQL Server Analysis Services (MSSAS).
Kerberos configuration
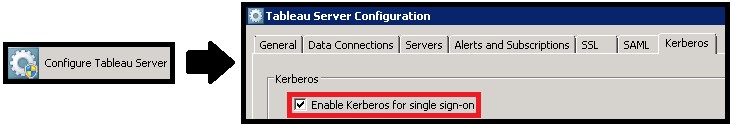
Kerberos is configured using the “Configure Tableau Server” application. The first step is to enable it in the “Kerberos” tab as shown below:
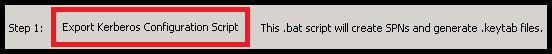
After enabling Kerberos, you must create the configuration script. In most cases you can simply use the default script generated by Tableau when you click the “Export Kerberos Configuration Script” button of the “Kerberos” tab:
This script has two steps:
- SPN registration: The Service Principal Name (SPN) registers the host in the Kerberos environment, so that services running on it can authenticate against other services.
- Keytab generation: The Keytab file contains the shared password provided by Kerberos that is used to authenticate against other services.
Example:
The default script registers the SPNs and generates the Keytab for the HTTP service in the host where Tableau Server is installed for the “Run as User” account using the setspn and ktpass commands.
For example:
setspn -s HTTP/tableauhost DOMAIN\runasuser setspn -s HTTP/tableauhost.domain DOMAIN\runasuser ktpass /princ HTTP/tableauhost.domain@DOMAIN /pass runasuserpass /ptype KRB5_NT_PRINCIPAL /out keytabs\kerberos.keytab
There are some scenarios where the default configuration can be problematic:
Scenario 1: Duplicate SPN
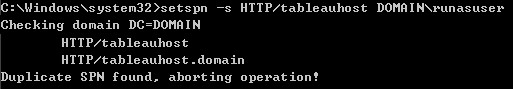
In some environments, another service might have already registered an SPN for the HTTP service in the host where Tableau Server is installed. An example could be a web server installed in the same host. If this already-existing SPN has been registered for a user other than the Tableau Server “Run as User” you will get an error, since duplicate SPNs for the same service/host pair are not allowed:
There are two ways to overcome this problem. If the existing SPN is not used anymore, you can delete it using the setspn –D command, and then create the new SPN without any problem. If the old SPN is still being used, it will be mandatory to use the user for which the existing SPN was created as the Tableau Server “Run as User”.
Scenario 2: Multiple host aliases
It is common to use an alias that is different from the host name to access Tableau Server. For example, you might connect to http://tableau.domain.com, instead of using http://tableauhost. If using an alias registered in your Domain Name Server (DNS), you will have to create SPNs for all of them.
For example:
setspn -s HTTP/tableau DOMAIN\runasuser setspn -s HTTP/tableau.domain.com DOMAIN\runasuser
In this case, you will also need to generate a Keytab for each alias. However, Tableau Server only allows one Keytab file. Therefore, you will have to nest all the Keytab files, one by one (for each alias). To do so, you can use the option \in of the ktpass command.
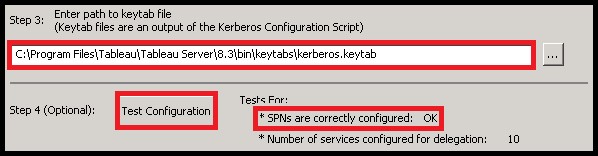
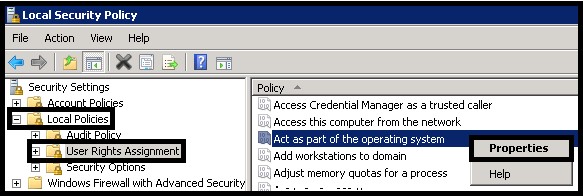
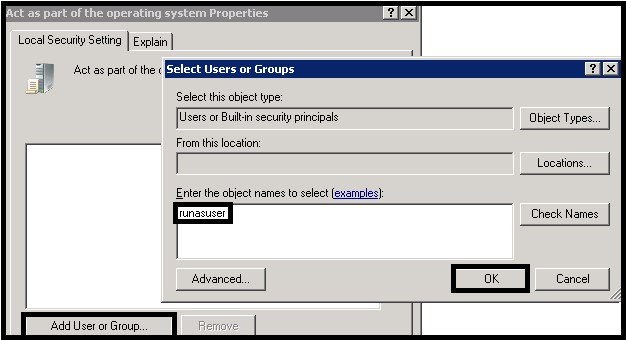
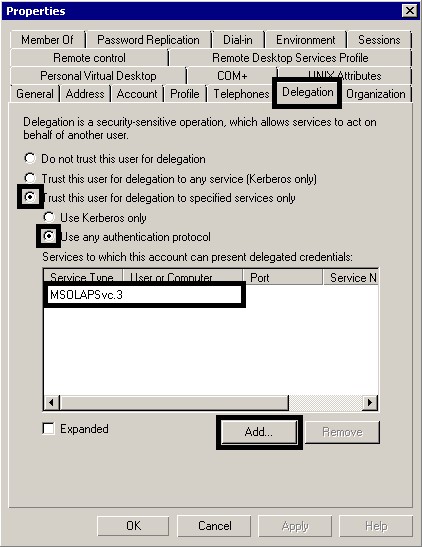
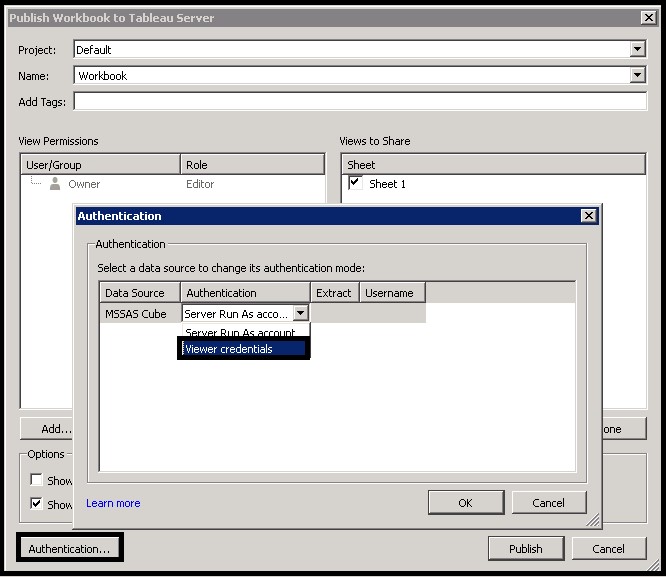
For example: ktpass /princ HTTP/tableauhost.domain@DOMAIN /pass runasuserpass /ptype KRB5_NT_PRINCIPAL /out keytabs\kerberos_1.keytab ktpass /princ HTTP/tableau.domain.com@DOMAIN.COM /pass runasuserpass /in keytabs\kerberos_1.keytab /ptype KRB5_NT_PRINCIPAL /out keytabs\kerberos_1.keytab The intermediate file names are not important, but the last Keytab file must keep the name “kerberos.keytab”. The script will have to be executed from the Command Prompt (CMD) by a user with domain administration rights. After running the script it is important that no error messages appear while registering the SPNs and that the Keytab file has been generated. Finally, import the Keytab file into Tableau Server and test the configuration. If everything is correct, you will receive an OK message after the test. If you restart Tableau Server now, the users of Active Directory will be able to use the SSO feature. The use of Kerberos delegation to Microsoft SQL Server Analysis Services (MSSAS) is very useful from a security point of view. If you have security roles defined in your OLAP cubes for the Active Directory users, the users will only see the information they are allowed to see without including any extra security in the Tableau workbooks. In order to enable the delegation to MSSAS, first configure the “Run as User” account to act as part of the operating system. For that purpose, open the Local Security Policy application from “Start –>Administrative Tools –> Local Security Policy”. Once there, go to “Local Policies –>User Rights Assignment –> Act as part of the operating system (right click) –> Properties”. Finally, click on “Add User or Group…” and add the “Run as User” account. After this step, you will have to configure the services that will be delegated. This has to be done by an Active Directory administrator using the Active Directory Administrative Center. Find the “Run as User” account in the list and right click to enter the “Properties” menu. From there go to the “Delegation” tab and select the options “Trust this user for delegation to specific services only” and “Use any authentication method”. Finally, click on “Add…” and select the MSSAS service from the list of available services. The MSSAS services will have names like “MSOLAPSvc.3”. It is important to keep in mind that, whenever you upload a workbook to Tableau Server, if you want the Kerberos delegation to be used, you will have to configure the authentication options. In this case, select “Viewer credentials” as the authentication method for the MSSAS data source. Authentication delegation to MSSAS